
Rating of the best access control and management systems (ACS) for 2022
With the expansion of the range of potential threats, much attention is paid to ensuring and maintaining security at facilities - from educational institutions or offices to large business centers or enterprises. Together with the usual full-time security officers who perform these functions, technical means and systems are actively used that significantly improve the capabilities of the security service.

Now the market has a large selection of such devices, both Russian and foreign production. The Security Technologies forums that were regularly held before the coronavirus pandemic brought together representatives of dozens of Western brands and hundreds of domestic manufacturers on one site. Among the variety of products, choosing the optimal device is quite difficult. The ratings presented in the review will help you navigate among the range of models.
Recommended article about The best biometric access control systems.
Content [Hide]
- 1 What is it and why do you need
- 2 Principle of operation
- 3 Areas of use
- 4 Kinds
- 5 ACS components
- 6 Criterias of choice
- 7 Where could I buy
- 8 The best access control and management systems
- 9 Experienced tips - how to install an access control system
What is it and why do you need
Access control and management system (ACS) - a set of compatible technical devices and hardware and software to ensure access to the facility.

It is intended for limiting and fixing the entrance (exit) through the equipped sections of the passage with the operational control of employees, as well as the time of their stay in the restricted area.
It is an integral part of the overall security system.
Main functions
- Authorization - identifiers are assigned, biometric features are determined; their registration with the task of time intervals and the level of access (when, where, who is allowed).
- Identification - identification by read identifiers or signs.
- Authorization – verification of compliance with the specified permissions.
- Authentication - determination of reliability by identification features.
- Implementation - permission or prohibition based on the results of the analysis.
- Registration - fixing actions.
- Reaction - measures in case of an unauthorized access attempt: warning and alarm signals, blocking the zone, etc.
Tasks
- Setting or disarming according to the established regulations, in emergency situations - recording and storing information.
- Remote online control.
- Access control in accordance with official authority.
- Identification and control of the movement of employees at the facility, preventing re-entry using the same identifiers.
- Accounting for working hours. Fixing the time and date of arrival of an employee at a specific place with a record of the duration of his stay there.
- Integration with other security elements - security, fire, video surveillance.
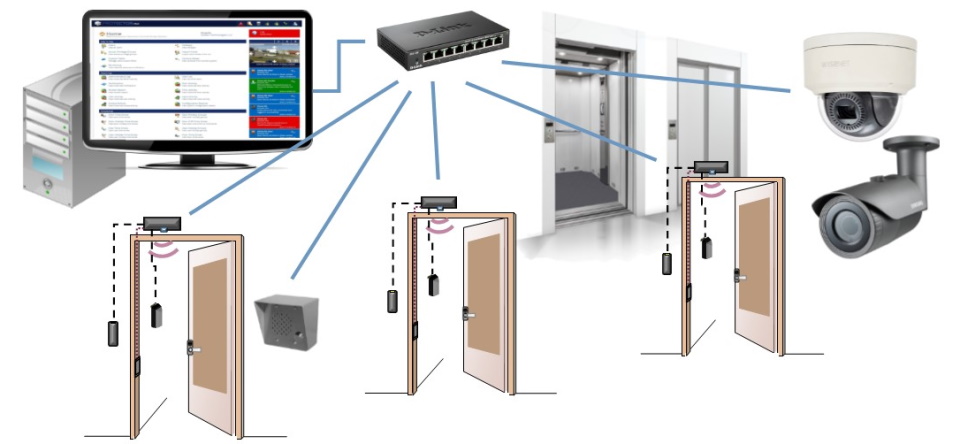
Principle of operation
Based on the comparison of various identification features of a person or vehicle with the parameters in the ACS memory. Everyone has a personal identifier - a code or password. Biometrics can also be used - face image, fingerprints, hand geometry, signature dynamics.
Devices for entering data or reading information are installed near the entrance to the closed area. Then the material is transferred to the access controllers for analysis and the appropriate reaction - to open or block the door, turn on the alarm or register the employee's presence there.

Areas of use
ACS installation locations:
- government;
- banks and financial organizations;
- business centers;
- enterprises, warehouses, closed territories;
- educational institutions;
- cultural and sports facilities;
- hotels;
- residential buildings, apartments;
- parking lots.

Kinds
By type of management
- Autonomous - passage without operator control and report to the central console.
- Centralized – access is allowed by the central console.
- Universal - the ability to switch to autonomous operation in the event of a malfunction of network equipment, a break in communication, a failure of the central console.
By number of control points
- Small capacity - up to 64.
- Medium capacious - up to 256.
- Large capacity - over 256.
By functionality class
1. The first is limited functionality.
Autonomous systems with the simplest set of functions for small objects without the need to combine controlled objects into a single complex with centralized control. The complete set includes an executive element, the reader and the controller. An example is budget locks with electronic key carrier readers or built-in code dialers. It is possible to connect exit buttons, opening reed switches, IR sensors.

2. The second is advanced features.
Inexpensive complexes based on several controllers with an increase in the amount of processed information and the number of users, as well as the obligatory use of a computer for programming all controllers, collecting and analyzing information, compiling reports and summaries, and effectively monitoring the situation at the facility.

3. The third one is multifunctional systems.
The best multi-level network complexes for a large number of users with controllers connected in local networks, which are offered by the best manufacturers. They are used when it is necessary to control the passage time using complex electronic identifiers.
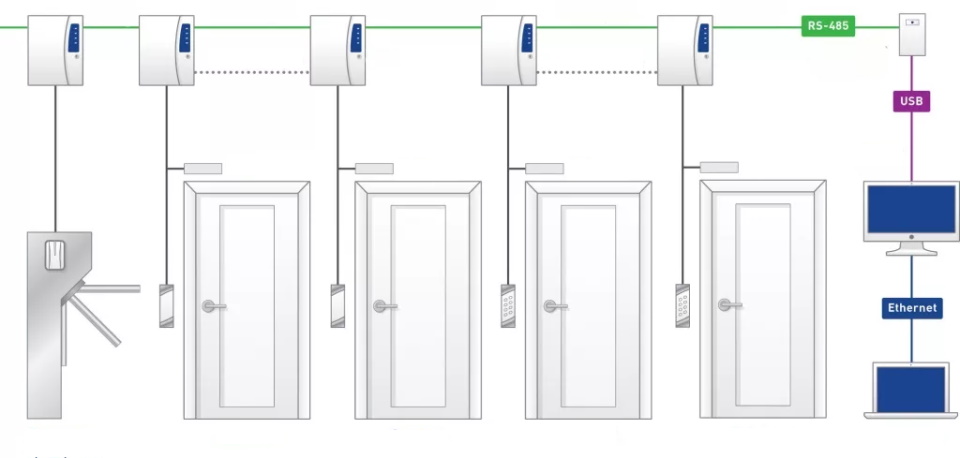
According to the degree of protection against unauthorized access
- Normal.
- Elevated.
- High.
ACS components
Blocking devices
Technical structures for a physical barrier against unauthorized entry into the facility.
one.Turnstiles - to organize the identification of any person entering the facility. Structurally, there are:
- waist;
- full height.

2. Doors - for passage to a room or territory. Equipped with actuators:
- electromagnetic latches - triggering when power is applied or removed;

- electromechanical locks - the action of the opening impulse before opening and closing the door;

- electromagnetic locks - opening when the power is turned off;

- drive mechanisms.
3. Sluice cabins - for blocking with additional confirmation of identity.

4. Gate - for the passage of standard vehicles.

5. Barriers - for the passage of overall vehicles.

6. Bollards - rising structures to block entry.

Identifiers
Devices for storing data that determine the owner's rights for access. They differ in the use of recording technology. Access methods:
- radio frequency identification (RFID) - key fob or plastic card;

- virtual identification - random code generation by a special application in a smartphone;

- by mobile phone number;

- password - entering a PIN code on the panel;

- biometric identification - by unique human characteristics.

Readers
Identification code receivers for translation into the decision block. Work with certain identifiers, reading is performed:
- for magnetic cards - from a tape;

- for Touch Memory keys - on contact;

- for Smart-cards - from the built-in chip;

- GSM - by phone number;

- biometrics - according to the individual characteristics of a person, converted into a digital sequence;

- PIN code - a set of certain combinations;

- contactless - using radio frequency RFID interaction.

Controllers
An electronic unit for analyzing the received data and generating a command for the action of actuators. According to the method of management, there are varieties:
- autonomous - work independently and are not included in a single system;

- network - operate in conjunction with the same models under a single control.

Software
Provides development of control algorithms for all ACS components. Installed on a computer or a separate server of the central console, depending on the capacity of the package.

Auxiliary equipment
If necessary, a security system with video surveillance, fire alarms, door opening sensors, elevators, breathalyzers, uninterruptible power supplies, etc. are additionally connected.

Criterias of choice
Each system is designed with the following factors in mind:
- Tasks assigned to ACS - future parameters are affected by their number and features.
- The need for additional functions and interfacing with other means - the connection of video surveillance cameras, biometric sensors, turnstiles, readers, identifiers.
- Type of access control system according to the size of the object - in a small store, autonomous equipment is enough, and when servicing a business center or a corporation, it is necessary to deploy a multi-level network complex.

Experts advise - what to look for in order to avoid mistakes when choosing:
- prior to the implementation of ACS, fully examine the facility to determine the optimal location of checkpoints, where the passage will be free without creating queues;
- clarify possible integration with other security elements;
- determine the design of devices to ensure safety from external and climatic influences;
- calculate the minimization of the impact on the stability of communication in the ACS of electromagnetic radiation from power cables passing in the immediate vicinity;
- check the performance and compatibility of the software with the required number of employees;
- provide for situations with controller overheating in case of a large throughput flow;
- install an emergency power supply;
- order a batch of passes in accordance with the installed access control system, taking into account possible damage and loss.
Where could I buy
Many foreign and Russian manufacturers compete fiercely with each other in the market. Leading those who offer a full range of equipment for the installation of ACS.
The determining factors are the price and quality of software and controllers.

According to Yandex search queries, the list of popular manufacturers includes:
- Russian brands - PERСo, Parsec, RusGuard, IronLogic, Era of New Technologies, ProxWave;
- foreign companies - Hid Global, ZKTeco, Suprema, NedAp, Hikvision.
On the page in the online store, you can order online new items and popular models. Description, specifications, features, photos, connection instructions are available there.
ACS installation is carried out by specialized companies that are able to implement a full cycle from design to delivery of the entire architecture at the facility. At the same time, experts will give useful advice and recommendations - what are the access control systems, which company's devices are better to choose, how to choose, which component is better to buy, how much it costs.
The best access control and management systems
The rating of high-quality ACS components is based on reviews on the manufacturers' pages. The popularity of models, according to buyers, was determined by reliability, ease of installation and maintenance, durability, workmanship and price.
The review presents rankings among the best standalone and network type controllers.
TOP 4 best standalone access control controllers
AT-K1000 UR Box
votes 5

Brand - AccordTec (Russia).
Country of origin - Russia.
A compact Russian development for controlling 12/24V electric drives and controlling access at one point of passage to industrial or administrative premises, building entrances. Can be installed separately or inside actuators. Manufactured on a board placed in a compact plastic case. Installed informative indication and door position sensor.
With the reader iButton provides nine modes of operation. The set mode is stored in memory with automatic transition to it when the power is turned off and then on again. With proximity card readers supporting Wiegand protocols, provides four modes. The kit includes a jumper for programming the device.
The average price is 960 rubles.
- support for iButton and Wiegand26 interfaces;
- the type of lock is chosen independently;
- opening the lock up to 255 seconds;
- prevention of incorrect inclusion;
- identification 1320 keys;
- indication;
- small sizes.
- clearly expressed were not identified.
Smartec ST-SC010
votes 2

Brand - Smartec (Russia).
Country of origin - Russia.
An autonomous model of domestic production for creating an independent access control system at remote sites without the need to organize additional communication channels with the central console. It is used together with an external reader. Security is increased by mounting the device inside the protected object. It is programmed by a master card or an infrared remote control. You can delete / add one card or a whole group, incl. in case of loss. Readers with Wiegand26/34 and keypad are supported.

Sold at a price of 1365 rubles.
- identification of up to 500 users;
- programmable relay operation time;
- work in pulse or trigger mode;
- the possibility of group registration;
- access blocking;
- with the function of copying keys for transfer to another controller;
- built-in audio alarm;
- LED indication.
- not detected.
Alice K-1 relay
votes 1

Brand - "Alice" (Russia).
Country of origin - Russia.
Universal Russian-made development for controlling access actuators. Installed both separately and in the castle. You can rearrange the memory chip. Designed for 1216 keys. It is usually used for access to office, industrial or warehouse premises, as well as entrances to residential buildings.
Can be found for 580 rubles.
- compactness;
- independent selection of the lock;
- switching time of the electric drive with power up to 255 seconds;
- audio and light indication;
- prevention of incorrect inclusion;
- low price.
- not detected.
Z-5R (mod. Relay Wiegand)
votes 4

Brand - IronLogic (Russia).
Country of origin - Russia.
Miniature model with power relay output for control of lock, opening button, card readers or contactors, external control of buzzer or reader LED, door position sensor. Suitable for installation in the castle or separately.
Operating modes:
- Normal - the use of ordinary or blocking keys;
- Blocking - use of blocking keys;
- Relay - works when the key is in the reader zone, turns off in case of absence;
- Accept - entering all keys into memory and forming a database;
- Trigger - turn on / off the lock by touching the key.

The price range is from 767 to 860 rubles.
- independent choice of lock;
- simple installation and connection;
- programming through a computer;
- prevention of incorrect inclusion;
- compactness;
- excellent value for money.
- not identified.
Video review of the controller:
comparison table
| AT-K1000 UR Box | Smartec ST-SC010 | Alice K-1 relay | Z-5R (mod. Relay Wiegand) | |
|---|---|---|---|---|
| Number of keys | 1320 | 500 | 1216 | 1364 |
| Interface with reader | iButton, Wiegand 26 | Wiegand 26, 34 | iButtonTM, Wiegand 26, 34, 37, 40, 42 | DallasTM (iButton), Wiegand 26, 34, 37, 40, 42 |
| Opening time, s | 0-255 | 1-99 | 1-255 | 0-220 |
| Supply voltage, V | 12 | 12 | 10-14 | 9-24 |
| Switching current, A | 4 | 2 | 4.5 | 3 |
| Dimensions, cm | 6.5x3.8x2.2 | 6.5x5.4x1.9 | 5.5x2.55x1.6 | 6.5x6.5x2.0 |
| Weight, g | 16 | 40 | 20 | 53 |
| Warranty, months | 12 | 12 | 12 | 12 |
TOP 5 best network controllers ACS
PW-400 v.2
votes 2

Brand - ProxWay (Russia).
Country of origin - Russia.
A universal model for controlling and managing access to industrial and residential premises, taking into account events and passage time. It is used as an element of the general access control system of a small office or a checkpoint of a large enterprise.Allows you to organize a passage to one object with control of entry / exit or to two different objects, as well as a burglar alarm.
Ability to identify up to 32 thousand keys. The memory stores up to 47 thousand events, 250 time zones and weekly schedules. It is produced in the form of a board without a case for embedded equipment when operating at low temperatures up to -40⁰С.

The manufacturer offers for 13,700 rubles.
- large non-volatile memory;
- two Wiegand ports;
- with the "anti-double" function;
- door contact input;
- simple maintenance;
- real time clock.
- not detected.
NC-8000
votes 2

Brand - Parsec (Russia).
Country of origin - Russia.
The basic model for use in ParsecNET when equipping an access point and an associated guard signaling. Controls any executive device for restricting passage (turnstile, lock) and alarm operation.
The database stores information on eight thousand keys. The memory contains 16 thousand events, time profiles (64) and holidays (32). Communication with a computer via Ethernet or Rs-485 channels.
The operation of the device, electric locks and other devices is provided by a built-in power source. It comes in a durable plastic case with space for a backup battery.

On sale for 22,250 rubles.
- large amount of memory;
- giving a signal in the absence of movement at the facility in the presence of people there;
- function of an open door until the exit of the user with the privileges of "owner";
- counting the number of people at the facility;
- issuance of identifiers with a time limit;
- setting the number of allowed access;
- recovery in case of power loss;
- scheduling;
- two card access.
- explicitly absent.
Video instruction for connecting NC-8000 to RS-485 line:
Gate-8000
votes 0

Brand - Gate (Russia).
Country of origin - Russia.
A universal basic model for use as the main element of the Gate CUD system when controlling access to industrial or residential premises, as well as accounting for the time of events and passage to the office. It is used when equipping access points - one double-sided or two single-sided. Support is provided for all common readers with the control of various actuators. Additional inputs allow you to connect fire and security sensors.
The non-volatile memory can store 16,000 keys, 8,000 events, and 7 schedules. Primary adjustment and programming are carried out using a computer or autonomously with the ability to add / remove keys, change the relay operation time. Combining into a line via RS-422 (RS-485) interface in network mode up to 254 controllers for connection to a control computer.
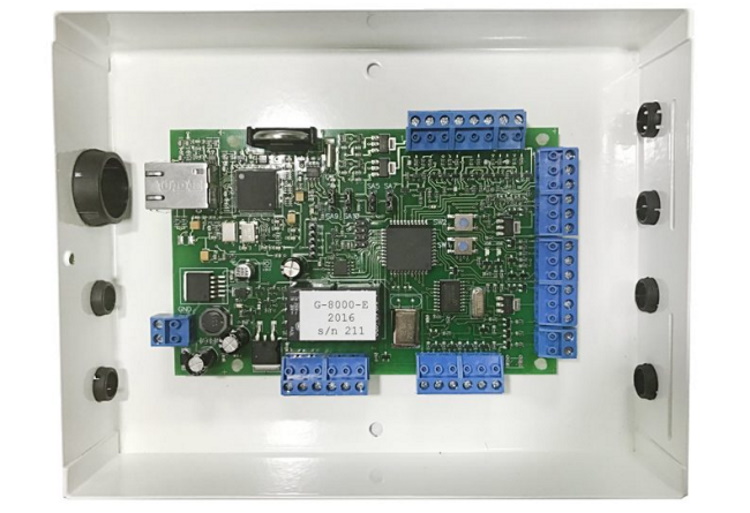
The average price is 4,780 rubles.
- large amount of memory;
- support for common readers;
- the possibility of autonomous or network operation;
- bringing up to 254 devices into the network;
- round-the-clock control of two security zones;
- in FreeLogic mode, control by events that the controller fixes;
- simple software;
- acceptable price.
- power supply is missing.
Gate basics:
Z-5R Net
votes 0

Brand - IronLogic (Russia).
Country of origin - Russia.
Compact model for stand-alone or networked CUD systems, including in a hotel or enterprise.Controls locks with electromechanical and electromagnetic drives. The turnstile requires two of these devices or an Extended model. The ability to identify 2024 keys, remembers 2048 events. Two inputs for readers with Dallas TM protocol support. The maximum distance of the communication line is 1.2 km. Five modes - Free Pass, Normal, Block, Trigger and Accept. Programming can be done via PC using an adapter

Sold for 2280 rubles.
- independent choice of lock;
- simple installation;
- easy connection via RS-485;
- the ability to restore the database in Accept mode;
- prevention of incorrect connection;
- small sizes;
- small price.
- not identified.
Video discussion of the capabilities of the X-5R Net controller:
ERA-2000 v2
votes 0

Brand - "Era of New Technologies" (Russia).
Country of origin - Russia.
Network model for installation in medium-sized facilities, in a hotel or small office with up to two thousand employees. The device is easily connected via Ethernet to the existing local network at the facility. Memory stores information about 60 thousand events. Serves two TouchMemory access points or one Wiegand4-64. Manages various executive devices - from locks and turnstiles to gateways and barriers. Electronic keys can be limited by the number of seats in the zone, the number of passes, time or time schedule.
The plastic housing contains two boards, one of which has a remote bar with terminals for connections to simplify installation and reduce the risk of human error. It is possible to reset to the installation settings.

The price from the manufacturer is 12,625 rubles.
- support for different types of electronic keys;
- saving up to 200 passage schedules in memory;
- availability of proprietary software;
- registration of access through an open door;
- hardware and software confirmation of the passage;
- clock with real time;
- offline programming;
- firmware with remote change.
- not detected.
comparison table
| PW-400 v.2 | NC-8000 | Gate-8000 | Z-5R Net | ERA-2000 v2 | |
|---|---|---|---|---|---|
| Number of electronic keys | 32000 | 8000 | 8167/16334 | 2024 | 2000 |
| Number of readers | 2 | 2 | 2 | 2 | 4 |
| Number of alarm inputs | 8 | 0 | 4 | 0 | 2 |
| Event memory size | 47000 | 16000 | 8192 | 2048 | 60000 |
| PC interface | USB, Ethernet 100 | Ethernet, RS-485 | ethernet | ethernet | Ethernet (IEEE802.3) |
| Supply voltage, V | 12 | 12 | 11,4-15 | 9-18 | 12-24 |
| Dimensions, cm | 12.5x10.0x2.5 | 29.0x23.0x8.5 | 20.0x15.5x4.0 | 6.5x6.5x1.8 | 11.2x12.5x3.3 |
| Weight, g | 1000 | 1400 | 1050 | 80 | 200 |
| Frame | plastic | plastic | plastic | plastic | plastic |
| Warranty, months | 12 | 12 | 12 | 12 | 60 |
| Place for battery | No | there is | No | No | No |
Experienced tips - how to install an access control system
To assemble a simple system with your own hands, you will need step-by-step instructions for actions and components:
- the lock, depending on the design of the door, is normally open or closed;
- key or access card;
- a reader suitable for a key or card is the best Mifare option that can work in a secure mode;
- autonomous type controller with a minimum set of functions;
- exit button;
- power supply that provides sufficient current.

The components are connected by a cable, the number of cores of which is determined by the installation diagram. Usually a six or eight core signal cable is used. When installing a lock on a door, a door transition is used for mechanical protection. The controller and power supply are mounted indoors on the wall in places with low traffic in a special case. The terminals are fastened according to the color instructions.
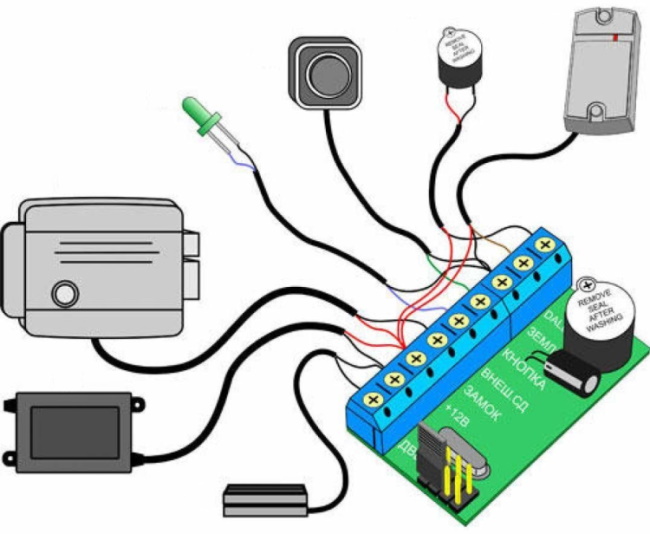
The program is configured after connecting all the elements. To create a database, you need to place the card next to the reader while the buzzer is sounding - the data will be automatically recorded and the signals will stop. Activate other cards in the same way.
As a result, the installed access control system should become a reliable protection for the facility.
Enjoy the shopping. Take care of yourself and your loved ones!
Popular Articles
-

Top ranking of the best and cheapest scooters up to 50cc in 2022
Views: 131650 -

Rating of the best soundproofing materials for an apartment in 2022
Views: 127690 -

Rating of cheap analogues of expensive medicines for flu and colds for 2022
Views: 124518 -

The best men's sneakers in 2022
Views: 124032 -

The Best Complex Vitamins in 2022
Views: 121939 -

Top ranking of the best smartwatches 2022 - price-quality ratio
Views: 114979 -

The best paint for gray hair - top rating 2022
Views: 113394 -

Ranking of the best wood paints for interior work in 2022
Views: 110318 -

Rating of the best spinning reels in 2022
Views: 105328 -

Ranking of the best sex dolls for men for 2022
Views: 104365 -

Ranking of the best action cameras from China in 2022
Views: 102215 -

The most effective calcium preparations for adults and children in 2022
Views: 102011
